
Angle

Moving Information Governance to the Driver’s Seat to Accelerate Cyber Breach Response
- Cyber Breach
- 3 Mins
Information Governance often takes a back seat to other organizational initiatives. But why is this the case? The list of reasons is long and varied. Not knowing where to start or how to build strategic approaches to governing information are top contenders. It is important to understand how nuanced this concept truly is and how it is has shifted in recent years. Also consider what other initiatives may intertwine.
Harmonizing information governance and cybersecurity is a great place to start that will have an immensely positive downstream effect. This can minimize business disruption and regulatory risk while also improving ROI. Information governance is often viewed as discretionary spend, so combining with cyber efforts will increase ROI and outweigh any unplanned emergency costs resulting from a breach.
Modern Day Information Governance
Information governance encompasses the policies, processes, and controls that enable organizations to manage their information assets effectively. Many layers are involved as these initiatives need to address legal, regulatory, and compliance requirements while aligning information with business objectives. Take a look at the IGRM model that was revised last year to encompass all the components that feed into a robust and effective information governance program.
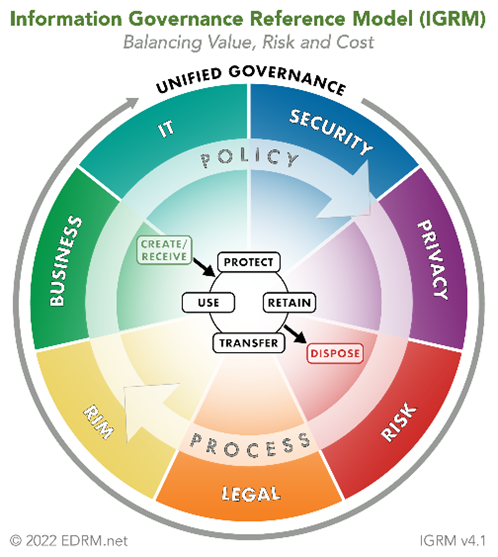
This model illustrates modernized information governance. Priorities has shifted due to new tools for managing data, expanded use of AI for business processes, and ever-evolving legal and regulatory landscapes. Upon releasing this, the EDRM proclaimed: “Sound information governance is increasingly important in this information age, characterized by the proliferation of data, and the need for businesses to get the most value out of their data, while also complying with regulatory requirements, meeting litigation discovery demands, and protecting against security risks.” It is no surprise that security was emphasized, as clear information governance is critically important to limit the consequences that could result from a substantial data breach.
Considering Cybersecurity
Cyber incidents happen daily. They threaten an organization’s data management and retention capabilities, business operations, and client relationships. Significant liability can ensue after an attack, which has placed proactive breach planning as a top initiative for many. In IBM’s 2023 Cost of a Data Breach report, 51 percent of organizations said they plan to increase cybersecurity spending because of an internal breach. To bolster these efforts, information governance and cybersecurity need to intertwine.
Cloud-based information governance is trending in response to data privacy obligations, the need for tighter security, and ever-increasing amount of digital data. Being able to reduce breach risk by considering cybersecurity during cloud migration is an added benefit. Cyber insurance carriers are also imposing a higher level of scrutiny before writing a policy, so this is a way for organizations to illustrate strong security protocols.
As companies continue to move to the cloud and attempt to reduce spend on information technology, it is becoming more important to be creative in where investments are made across people, process and technology. Information governance is an area of opportunity to invest in to reduce the risk associated with cyber events.
Spend must also be thought of multidimensionally and holistically. Organizations must look beyond the cost to deploy and procure a solution. Increasing spend upfront in implementation and functionality can lead to reduced spend longer term by avoiding cyber events and minimizing the impact and cost of those that do occur. Think about costs associated with ransomware events, cyber counsel, business disruption to brand value, and the inability to do business for a period of time. The corollary of reducing spend also increases ROI, as tools bought for IT and privacy purposes may be applicable to security.
Exploring Solutions
An outside consultant can help mitigate the risk of cyber incidents by reducing the volume of data stored in a legally defensible manner. With stronger retention, organization, and encryption policies, there is less data available to intercept or access in the event of a breach. This greatly accelerates response efforts as there is less to sort through. This also offers deeper knowledge of where sensitive information resides and if it can actually be accessed by those outside of the organization.
Sometimes organizations already own technology that can help, but they are not taking advantage of the full potential. For example, in the Microsoft 365 environment there are several options available to better leverage an organization’s investment in this technology.
Some areas to explore related to information governance include:
- Data Classification: Consider implementing sensitivity labels, sensitive information types, and trainable classifiers to foster cybersecurity readiness.
- Data Lifecycle Management: Leverage M365 retention policies and labels to place the organization in a better position to defensibly delete data and reduce risks associated with over retention.
- Records Management: There are file plan capabilities and label policies that allow organizations to build a comprehensive solution to manage business-critical data in compliance with regulations, laws, and unique records retention policies.
- Communication Compliance: Many organizations are faced with industry and government regulations requiring them to monitor and review a defined percentage of communications. This is to comply with industry regulations, reduce other areas of risk, and increase security. Leverage expertise in emerging technology such as Microsoft 365 to address these requirements and augment processes with staffing to manage overall workflow.
- Insider Risk Management: The single largest risk for data theft and leakage comes from internal staff, disgruntled workers, and employees looking to leverage corporate information at their next job. Most organizations are still taking a reactive and forensic approach to investigate insider risk. Predictive solutions become very cumbersome and expensive due to the volume of data that needs to be analyzed to identify risk. There are solutions that allow companies to identify triggers, trends, and events that often lead to data theft – or at the very least minimize or mitigate the loss when the theft occurs.
- Information Protection and Data Loss Prevention: Many organizations are faced with industry and government regulations requiring them to monitor and prevent dissemination of data outside of the organization. This includes HIPAA, Export Control, PCI, PII, and more. Managing and monitoring such data is of critical importance. Additionally, many organizations had to rush to cloud services during the onset of the pandemic to provide employees remote work access. Due to the expedited nature of migration, most concentrated initial efforts on providing connectivity and securing authentication. Now these organizations are refocusing their efforts on protecting data. Microsoft and other tools offer solutions that allow organizations to identify sensitive data, monitor it, and apply protective controls.
All of this can feed into cyber initiatives by allowing organizations to leverage the value in their data while effectively managing security and compliance. Now is the time to move information governance out of the back seat and make it a key driver for cyber initiatives.
The contents of this article are intended to convey general information only and not to provide legal advice or opinions.
